Introduction
This is part 2 of my series on IBM Cloud – Provisioning a Cloud Server. In this part, we will perform several tasks to improve the virtual server’s security and access.
- Review hardware firewall options.
- Lockdown external access by creating and attaching security groups.
Hardware Firewalls
IBM Cloud offers several firewall options to protect your virtual servers. These options are shared and dedicated firewalls. IBM’s firewall options are not available for hourly billing instances. This means that you must select monthly billing.
A hardware firewall is a device that protects the virtual server by blocking traffic before the traffic reaches the server. IBM’s shared firewall leverages a multi-tenant architecture to protect individual servers. For 100 Megabit network links, the pricing is $99.00 per month. Traffic that is blocked by the firewall does not count against your monthly bandwidth allotment.
The IBM shared firewall provides the following features:
- Intended Use: Single Server Primary IP Protection
- User Interface: Integrated into SoftLayer Control Portal and SoftLayer API
- Features: Stateful Packet Inspection, Ingress Firewall Rules, IPv4, IPv6, Basic Logging
- Throughput: 10Mbps, 100Mbps, 1000Mbps, or 2000Mbps
Since we chose hourly billing for our test instance, we will not be configuring an IBM Cloud firewall in this article. I plan to write an entire article on the IBM firewall.
For more information on IBM Cloud Firewalls, go here.
Security Groups
IBM Cloud security groups are IP filter rules that define how to handle incoming and outgoing traffic. Security groups can be assigned to the public and private network interfaces. A security group can be considered a type of software firewall.
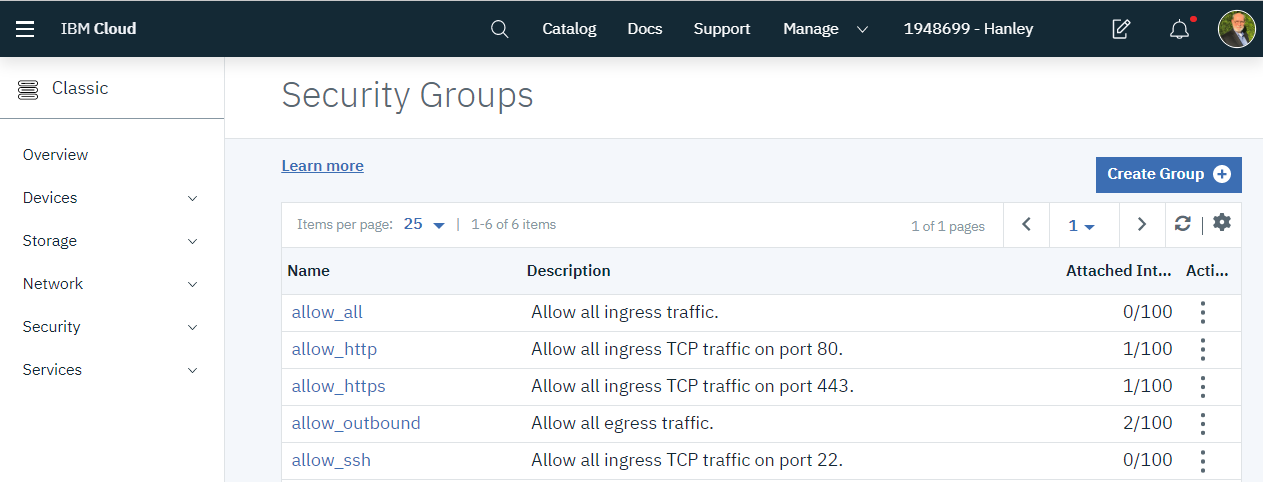
IBM Cloud provides several predefined security groups:
| Name | Description |
|---|---|
| allow_ssh | This security group defines the IP rules that allow ingress TCP traffic on the SSH port only (22/TCP). |
| allow_http | This security group defines the IP rules that allow ingress traffic on HTTP port only (80/TCP). |
| allow_https | This security group defines the IP rules that allow ingress TCP traffic on HTTPS port only (443/TCP). |
| allow_outbound | This security group defines the IP rules that allow all egress traffic from the server. |
| allow_all | This security group defines the IP rules that allow all ingress traffic on all ports. |
For this article, we will create a new security group that only allows SSH traffic from our IP address.
Security groups can be assigned to a network interface while a virtual server instance is running or stopped. However, assigning a security group to a network interface does not take effect until the instance is rebooted.
Security group rules can be modified while an instance is running and take effect immediately for new connections. Security group rule changes do not affect existing connections.
This means that if someone connected to a virtual server instance via SSH and you remove the rule that allows SSH connections, new SSH connections will be blocked. The existing SSH connections will not be blocked.
Go to the IBM Console -> Classic Infrastructure. Expand the menu Security. Expand Network Security. Select Security Groups. This link is a shortcut.
Review the existing security groups.
Click on allow_ssh.
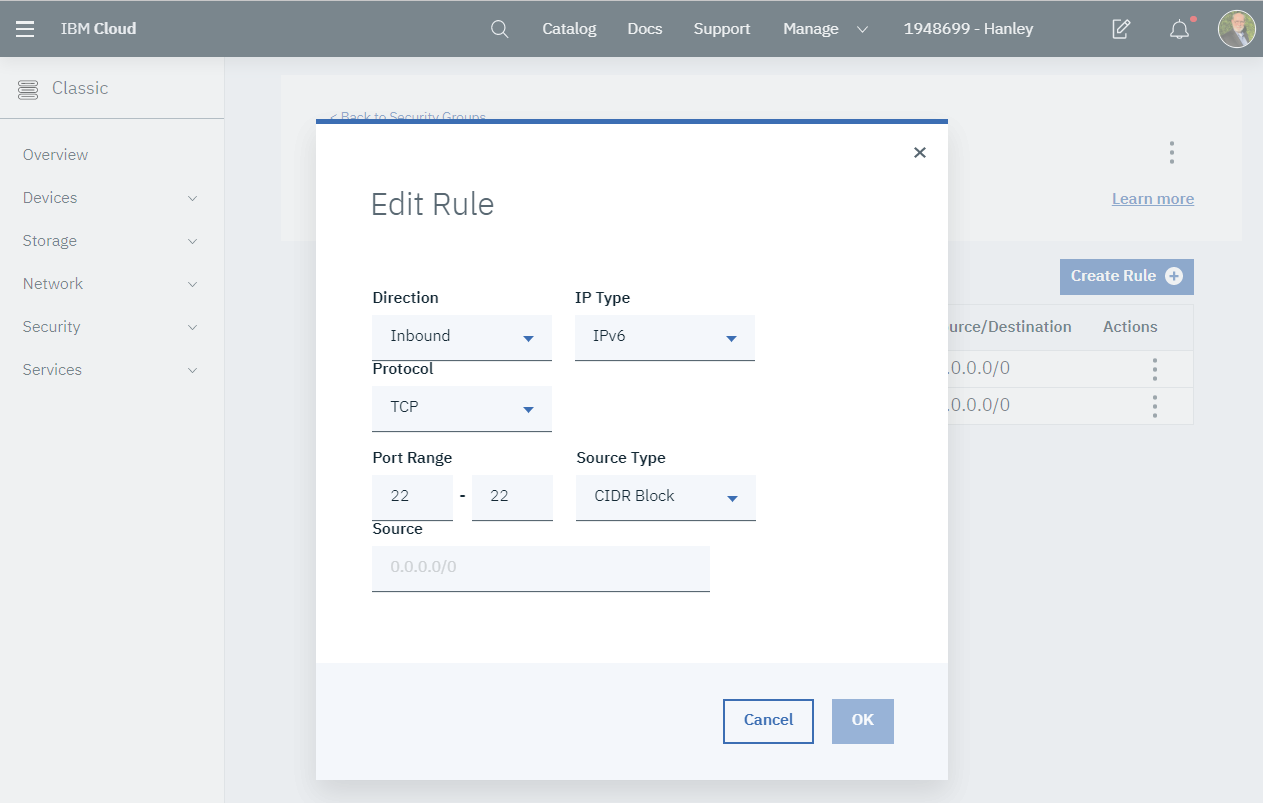
Notice that the security group has two Inbound rules. One for IPv4 and another for IPv6. The Port Range is 22. Click on the IPv6 vertical ellipsis menu under Actions. Select Edit.
Click on the Source Type drop-down. Notice that you can specify a CIDR Block or a Security Group. Press the Cancel Button. Repeat for the IPv4 security group rule. Click the back arrow to return to the security groups page.
We will now create a rule for access from the office.
The first item that you will need is your office’s IP address or CIDR address block. If this information is not available, go to this endpoint in your browser which will display your public IP (IPv4) address.
https://www.jhanley.com/test/getmyip.php
You can also use curl with this endpoint:
|
1 |
curl https://www.jhanley.com/test/getmyip.php |
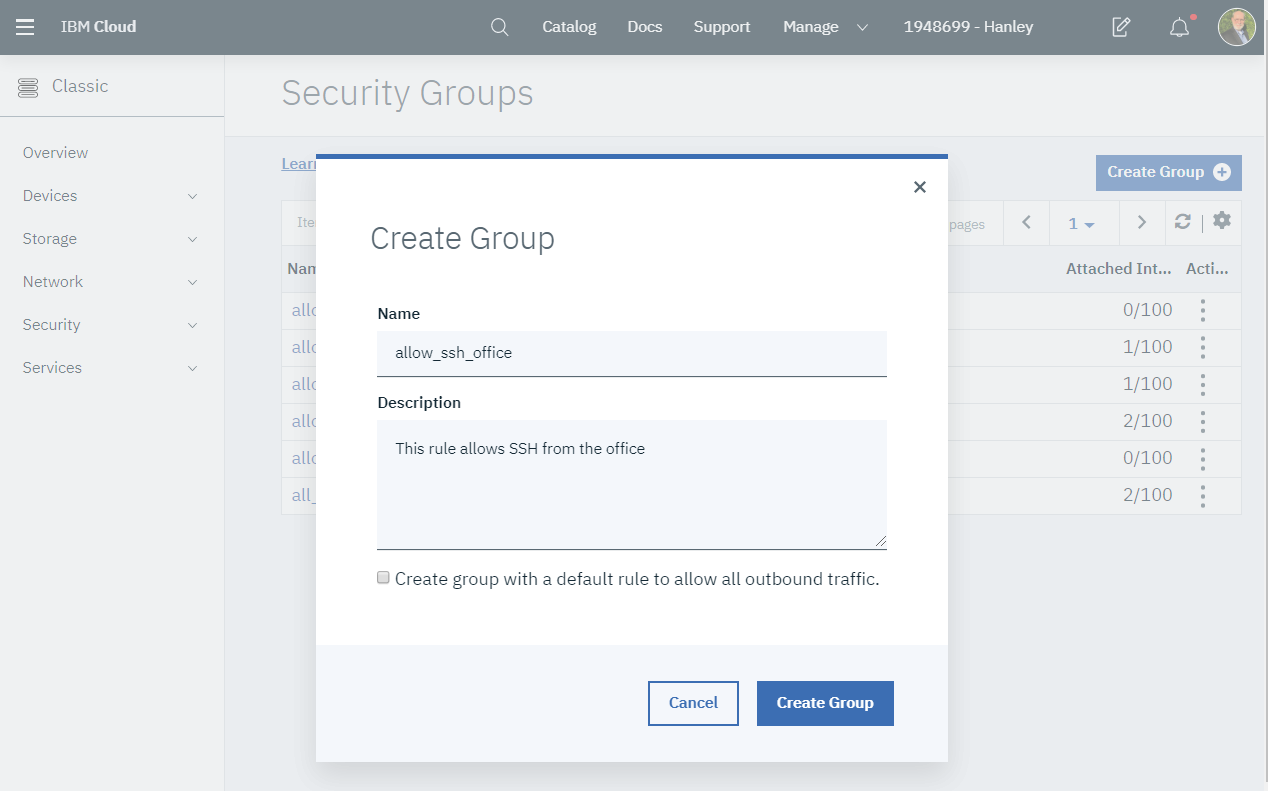
Click the Create Group button. A dialog will appear. Enter the following information:
- Name: allow_ssh_office
- Description: This rule allows SSH from the office
- Deselect “Create group with a default rule to allow all outbound traffic”
Press the Create Group button.
By default, this new rule allows all outbound traffic. This rule is not yet assigned to a virtual server, so rule this is harmless.
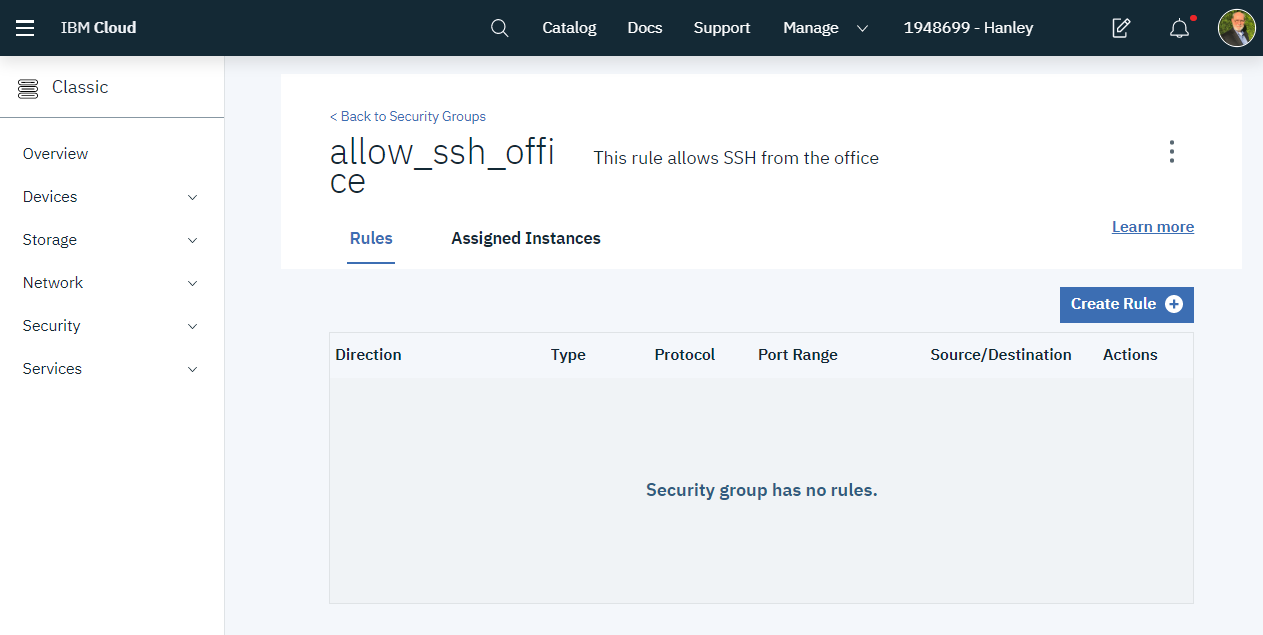
Click on the new rule under the column Name. This displays a new dialog box.
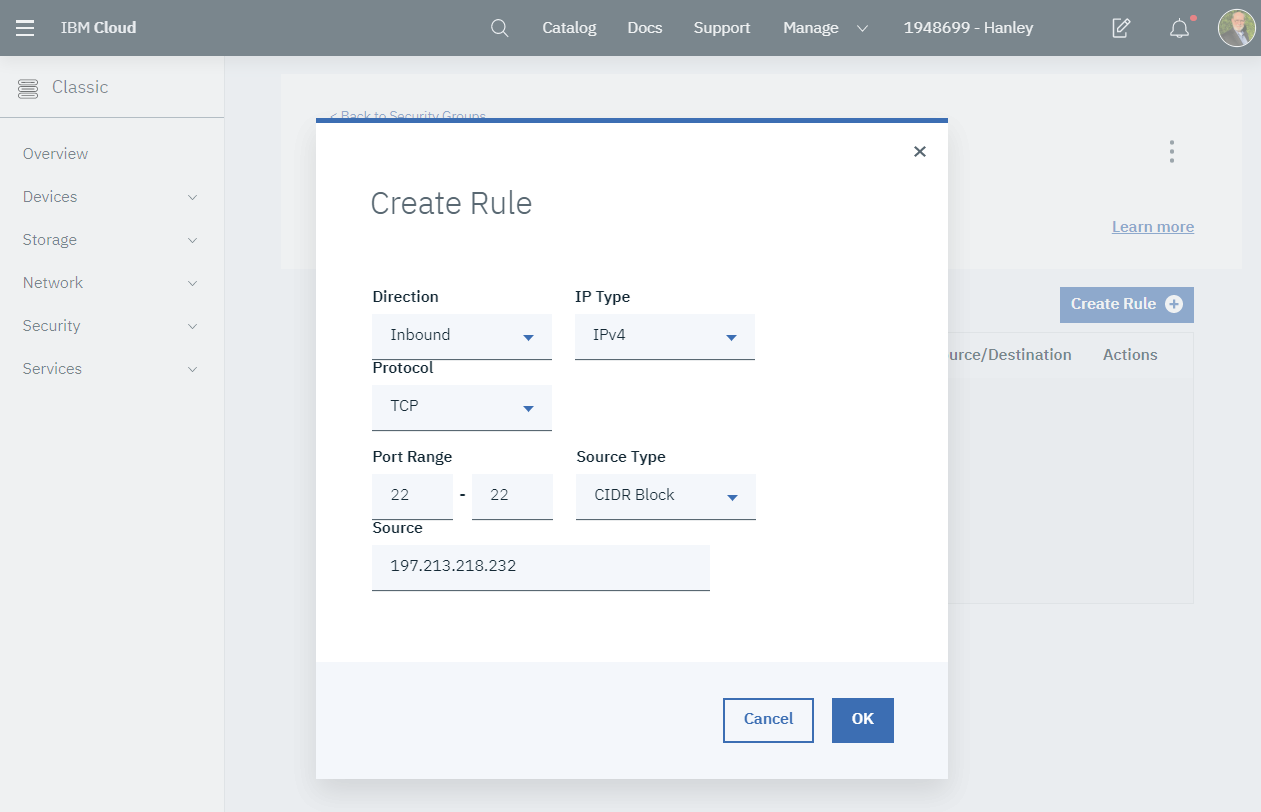
Click the Create Rule button. Complete the new rule after reviewing this screenshot. Use your IP address for the Source.
Click the back arrow to return to the security groups page. Now we will assign this security group to the virtual server instance.
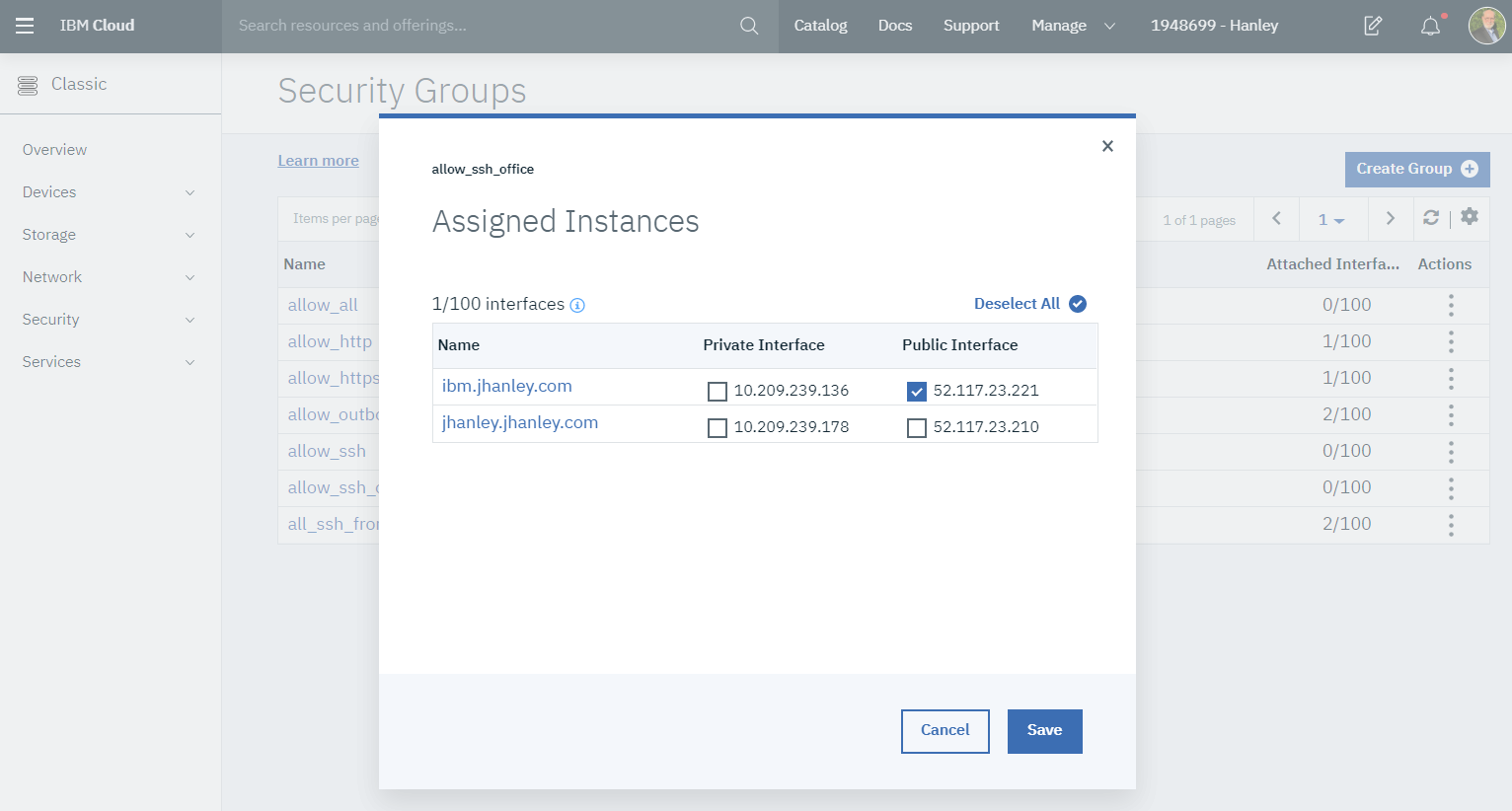
To the right of the new security group is the vertical ellipsis menu. Click and select Manage Instances. A dialog appears. Select the Public Interface for the virtual server instance and then click the Save button.
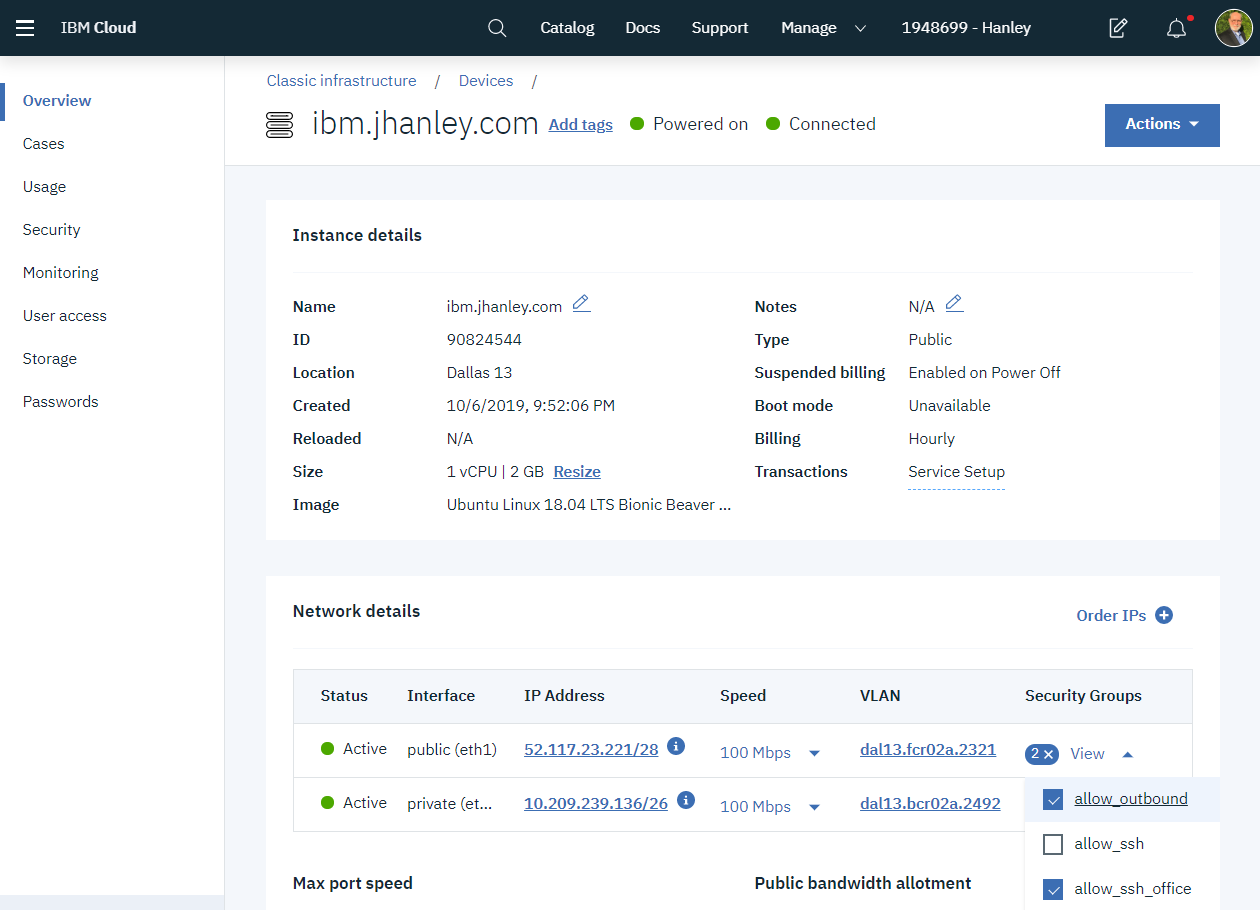
If we go back to the Device page for our instance, we can also review which security groups are assigned to our virtual server instance. Look at the bottom right of this image.
Advanced
Example CLI command to list security groups:
|
1 |
ibmcloud sl securitygroup list |
Example Output:
|
1 2 3 4 5 6 7 |
ID Name Description Created 1823498 allow_ssh Allow all ingress TCP traffic on port 22. 2019-07-27T06:46:46Z 1823500 allow_http Allow all ingress TCP traffic on port 80. 2019-07-27T06:46:46Z 1823502 allow_https Allow all ingress TCP traffic on port 443. 2019-07-27T06:46:46Z 1823804 allow_all Allow all ingress traffic. 2019-07-27T06:46:46Z 1823806 allow_outbound Allow all egress traffic. 2019-07-27T06:46:46Z 2052368 allow_ssh_office This rule allows SSH from the office 2019-10-07T14:48:59Z |
Example CLI command to create a security group:
|
1 |
ibmcloud sl securitygroup create --name allow_ssh_office -d "This rule allows SSH from the office" |
Example CLI command to add a rule to a security group:
|
1 2 3 4 5 6 7 |
ibmcloud sl securitygroup rule-add 2052368 ^ --remote-ip 197.213.218.232 ^ --direction ingress ^ --ether-type IPv4 ^ --port-min 22 ^ --port-max 22 ^ --protocol tcp |
For the above command, you will need the Security Group ID. This can be obtained with the security group list command: ibmcloud sl securitygroup list
Example CLI command to list the rules in a security group:
|
1 |
ibmcloud sl securitygroup rule-list 2052368 |
Example Output:
|
1 2 |
ID Remote IP Remote Group ID Direction Ether Type Port Range Min Port Range Max Protocol 6341424 197.213.218.232 - ingress IPv4 22 22 tcp |
Example CLI command to list the network interfaces associated with a security group:
|
1 |
ibmcloud sl securitygroup interface-list 2052368 |
Example Output:
|
1 2 3 |
ID Server ID Hostname Interface IP address 58069972 90774432 jhanley public 52.117.23.210 58116816 90824544 ibm public 52.117.23.221 |
Example CLI command to associate a security group with a virtual server network interface:
|
1 |
ibmcloud sl securitygroup interface-add 2052368 --interface public --server 90824544 |
Example CLI command to list the virtual servers to get the Server ID for the previous command:
|
1 |
ibmcloud sl vs list |
Next Steps
In this article, we discussed IBM Cloud firewalls and security groups. Then we created a new security group and added a rule that only allows SSH traffic from office. In the next part of this article series, we will perform several more tasks to improve the virtual server’s security and access.
- Create an additional user with sudo access.
- Create SSH keypairs for the new user and for the root user.
- Improve the SSH server security.
More Information
Documentation
- Getting Started with Security Groups
- What are security groups?
- Managing security groups for virtual server traffic
- Creating and working with virtual servers
- Managing classic infrastructure VLANs
YouTube: IBM Videos
- How to set up a web app with Security Groups, Load Balancer & CDN
- IBM Cloud Foundation Skills Series – Security Groups
- IBM Cloud Foundation Skills Series – Security Groups Lab
Credits
I write free articles about technology. Recently, I learned about Pexels.com which provides free images. The image in this article is courtesy of Edwin Rucci at Pexels.

I design software for enterprise-class systems and data centers. My background is 30+ years in storage (SCSI, FC, iSCSI, disk arrays, imaging) virtualization. 20+ years in identity, security, and forensics.
For the past 14+ years, I have been working in the cloud (AWS, Azure, Google, Alibaba, IBM, Oracle) designing hybrid and multi-cloud software solutions. I am an MVP/GDE with several.


Leave a Reply